Three Levels of Security to Render Hacking Tools Useless
There are many tools that makes it much easier for adversaries to hack IoT devices. Hardware tools can be used to expose insecure I/O interfaces, which is a steppingstone to access plaintext source code, U-Boot commands, or Linux root access. There is also an array of software tools that decompile binaries, simulate execution, and analyze code to find bugs that can be turned into cyber exploits. These are actually embedded system debug tools, but they are put to nefarious purposes.
It’s critically important to add cybersecurity to your IoT devices that specifically protect against these tools. With basic cybersecurity features, adversaries can be stopped dead in their tracks, leaving them to conclude your device is a well-secured target. Given they are looking for the easiest targets to exploit, there is a good possibility they will move on, and your IoT device will remain secure.
This blog complements an article contributed to Embedded Computing Design titled Hacking the IoT Isn’t Rocket Science . That article goes into more depth on the features of the hardware and software hacking tools listed here. It also presents cybersecurity features that would have mitigated the vulnerabilities of using these tools found by security researchers Stephan Huber and Philipp Roskosch from Fraunhofer FIT. These researchers did excellent work finding vulnerabilities in over 33 different VoIP office phones. There are many security lessons learned from reviewing these phones' security flaws and how they were exploited.
Commonly used hardware hacking tools include JTAGulator and BuSPIrate. These tools require physical access, which is an everyday possibility for IoT devices. Consumer, healthcare, and even industrial and automotive IoT devices can easily be purchased from various sources (e.g., junkyards for automobiles, online, business liquidation). These tools can extract code/data, modify memory, and affect the device while running. Below is a summary of their features:
- JTAGulator: Uses a serial-terminal or USB interface to communicate to a PC. This tool makes connecting to the on-chip debug interfaces such as JTAG/IEEE 1149.1, ARM Single Wire Debug (SWD), and UART much easier. If the interface is not known, a JTAGulator will detect and identify it.
- BuSPIrate: Provides easy access to the many serial interfaces on an embedded processor, including SPI, UART, I2C, and JTAG.
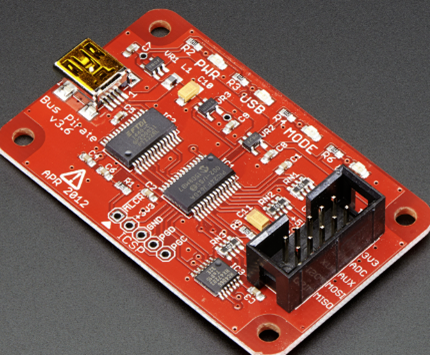
| JTAGulator: acceses open interfaces (JTAG, UART) |
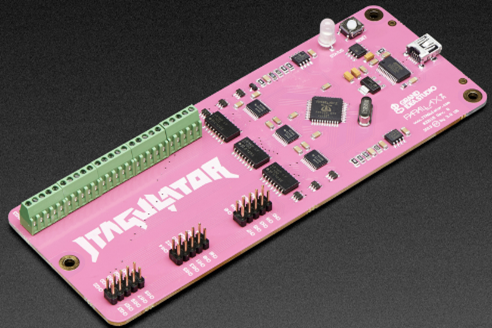
| BuSPIrate: accesses open interfaces (SPI, UART, JTAG) |
Software hacking tools help with decompilation of code, emulation of operating systems, and emulation of specific embedded processor instruction sets.
Commonly used tools include:
- QEMU: An open-source emulator that supports Linux and Windows emulation and of instruction sets including MIPS, ARM, and x86.
- Unicorn: It is based on QEMU but is lighter weight and offers several additional features.
- Ghidra: It is a reverse engineering tool that support decompilation of many different embedded processor instruction sets including x86, ARM, PPC, MIPS, MSP430, and AVR32
- IDA Pro: It is also a decompilation tool.

| QEMU: Open-Source CPU Instruction Set and OS Emulator |

| Unicorn: Lightweight CPU Instruction Set Emulator that Builds on QEMU and Adds Features |

| Angr: Tool for Static and Dynamic Symbolic Analysis of Code |

| Reverse Complication Tool Developed by the NSA |
The combination of one of the hardware tools, a decompilation tool, and an emulation tool gives all that is needed to extract code from an IoT device, decompile, and run the software. These tools give adversaries the ability to reverse engineer code and find software bugs that can be exploited. Extracting and reverse-engineering plaintext code is one of the first things hackers attempt because quite often, it can lead to many and severe vulnerabilities.
The first level of security to protect against these hacking tools is to lock all serial interfaces. This security control will prevent easy access to memories where the code resides. Some processors, such as NXP's I.MX 6 and 8 and Analog Devices SHARC processors, have in-silicon features to lock interfaces with a password. These particular processors offer this security feature for their JTAG interfaces. Other serial interfaces like SPI, USB, and UARTs should ideally be disabled if not in use. If in use, access should only be granted with a password, or the devices being accessed are authenticated. Strong passwords should be used, and the software implementation of the password-based scheme should consider protections against side-channel attacks (e.g., drop power to the processor at the right time, so password code is skipped).
The second level of security is to encrypt code and data that is stored in non-volatile memory. If the first level is breached (i.e., flash memory is directly accessed), this second level provides protection. Encrypted code cannot be reverse-engineered as long as it is based on a secure encryption algorithm (e.g., AES-XTS for block memory devices) and uses a key of suitable length (e.g., AES with a 384 bit or higher key is even quantum computer resistant).
The third level of security is to protect code at run time. This will prevent security-sensitive code from being extracted from working RAM. The second level of protection, mentioned above, secures code and data at rest. This third-level protection secures code and data as it is being used. A trusted execution environment, such as that offered by the combination of Trust Zone and OP-TEE, enables security-sensitive code to run in protected memory that is very difficult for hackers to access. On-device Intrusion Detection System software detects a change in the operation of the device, such as when a hacker is attempting to extract code from RAM, and raises an alarm that the device is under attack.
BG Networks offers Consulting Services and Security Automation Tools to help you implement these three levels of security. Open-source code and in-silicon security accelerators are used in BG Networks solutions that reduce costs and development times and give the most secure implementations possible.
Our Security Automation Tools allow you to:
- Add security to your IoT devices even if you don’t have an extensive cybersecurity background
- Save time and R&D costs
- Enable security for trusted operation of IoT devices