AITHRA:
AI-powered Automation for Threat Modeling and Risk Assessment
10x Time Savings:
A New Approach for Cybersecurity Risk Management for FDA Submissions
Artificial Intelligence (AI) and Large Language Models (LLMs) substantially changes the way we create cybersecurity threat and risk assessments.
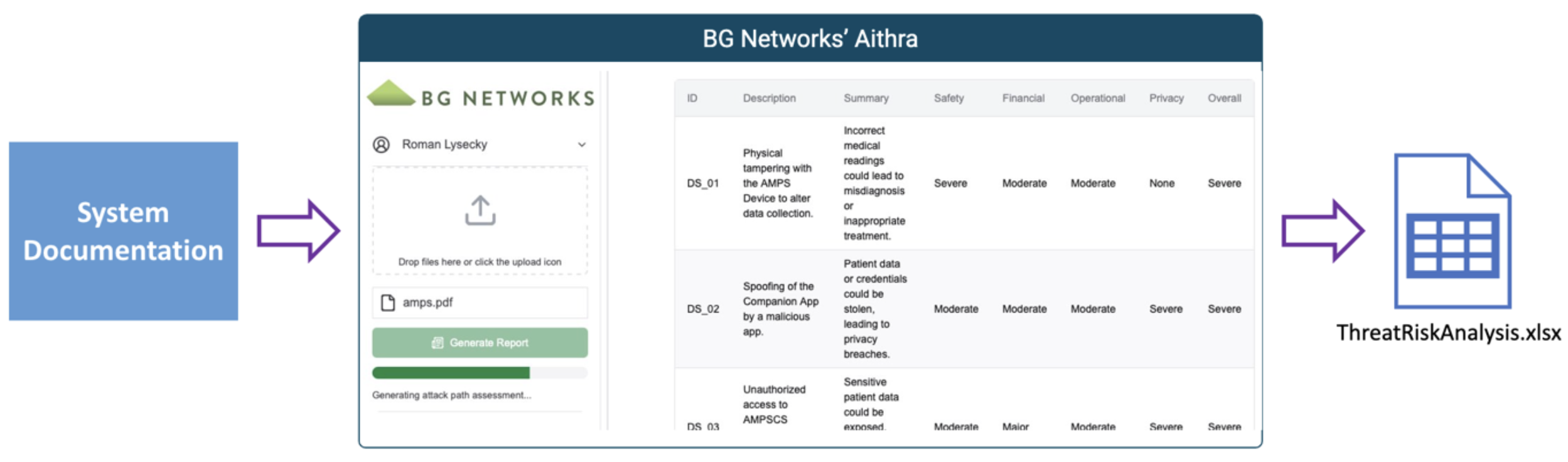
Aithra is a groundbreaking, LLM-powered Threat Modeling and Risk Assessment tool for medical devices that complies with FDA recognized standards.
With three steps, Aithra will generate an FDA compliant threat and risk assessment.
-
Gather existing medical device documentation and diagrams
-
Upload PDFs and/or images to Aithra
-
Click Generate Report
Contact us for a sample Aithra-generated threat and risk assessment or demo.
"*" indicates required fields
We created Aithra because the FDA mandates a risk-based Secure Product Development Framework (SPDF), from design to end-of-life. Compliance demands a structured, efficient approach—Aithra delivers exactly that. Aithra generates threat and risk assessment in minutes and exports data into spreadsheet-ready formats for easy integration with your SPDF documents and FDA submission.
For large and midsized companies, Aithra saves time for each new medical device submission to the FDA.
For small companies, who may not have dedicated cybersecurity resources or may be submitting for the first time, Aithra generates all the information the FDA expects and helps guide you in the process.
- 10x Efficiency Gains
Accelerate risk analysis and documentation with automated workflows for complex medical devices. - Supports Cloud, IoT, Phone Application, SaMD
All aspects of a medical device system are supported with comprehensive threat modeling and risk assessments. - Comprehensive output
More threats and risk identified than if done by hand. - FDA-Ready Threat and Risk Assessment
Generate reports in a structured format aligned with FDA requirements. - From Asset Identification to Risk Assessment
Define potential security risks, damage scenarios, and attack path enumeration with a structured threat modeling process. - STRIDE based Threat Modeling
STRIDE (Spoofing, Tampering, non-Repudiation, Information disclosure, Denial of service, Elevation of privilege) is broadly used and understood
- Flexible Input Options
Upload PDFs, images, and existing documentation in any format to streamline threat modeling and risk assessment. - Seamless QMS Integration
Ensure cybersecurity is embedded in your broader risk management process by evaluating safety risks identified by Aithra in your QMS risk process. - Early Design Risk Assessment
Perform a threat and risk assessment as soon as your system description is ready, gaining early visibility into necessary security controls and potential vulnerabilities. - Documents for eSTAR
Aithra creates information for eSTAR documents including “Threat Model”, “Cybersecurity Risk Assessment”, “Requirements” - Dynamic Risk Updates
Stay compliant with evolving threats by continuously updating risk assessments. (Coming soon)
Based on industry standards recognized by FDA: TIR57, ANSI/AMII SW96, ISO 800-30, & IEC 81001-5-1.
Process
Aithra generates risk assessment following systematic risk analysis process
Threat Modeling and Risk Amendment Process
Asset Identification
Define key system components and data assets.
Threat Modeling (STRIDE)
Identify potential threats using the STRIDE framework.
Damage Scenario
Assess the potential impact of security breaches.
Attack Path Enumeration
Map out possible attack vectors and entry points.
Attack Likelihood Analysis
Evaluate the probability of each attack scenario.
Risk Assessment
Prioritize risks and determine necessary security controls.